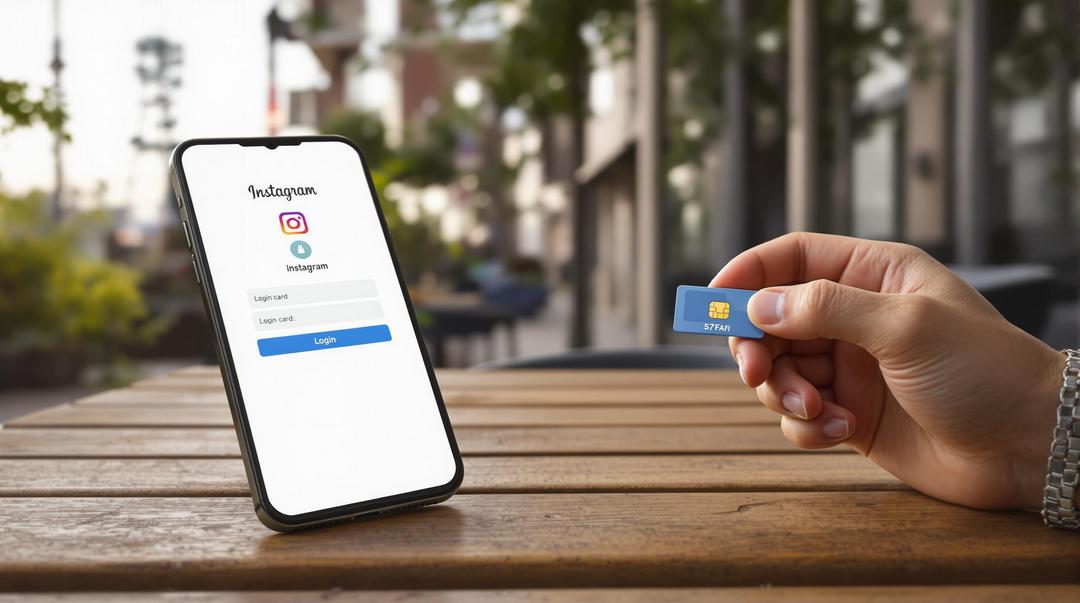
Social media hacking has garnered significant attention due to increasing digital threats and privacy concerns. One method that has raised alarms among cybersecurity experts involves the use of an SS7 Server for exploiting vulnerabilities in telecommunication infrastructure. This technique bypasses traditional security layers, making popular platforms susceptible to unauthorized access. Understanding the specifics of SS7-based vulnerabilities is crucial for anyone using social media today. How SS7 Protocol Weaknesses Affect Social Media Security SS7, or Signaling System No. 7, is a protocol suite critical to global telecommunications networks. It powers many core functions, such as text messaging, voice calls, and roaming. However, its design dates back to an era with lower…
カテゴリーアーカイブ: SS7 Hack
SMS intercept SS7 is a topic that has gained significant attention in recent years due to its implications for mobile security. With more people using SMS for authentication and communication, understanding the mechanisms behind interception is crucial. The term “SMS intercept SS7” refers to the technique of leveraging certain vulnerabilities in the telecommunication infrastructure to access text messages. This process relies on the architecture of SS7, a protocol that has become integral to global communication. Understanding SS7 and Its Importance Signaling System 7, commonly called SS7, serves as a backbone for telecommunication exchanges around the globe. First introduced in the 1970s, it enables communication between network elements, allowing seamless connections…
Modern telecommunications have evolved rapidly, but vulnerabilities remain that can be exploited for eavesdropping. One of the most significant of these is the use of the SS7 Server, which manages connections and data exchanges across global cellular networks. As telephony infrastructure relies on SS7 for routing phone calls and text messages, understanding its weaknesses is crucial. The ability to intercept calls through SS7 demonstrates both the remarkable connectivity and the persistent risks of our connected era. Understanding SS7 and Its Role in Telephony SS7, or Signaling System No. 7, is a set of protocols launched in the 1970s, instrumental for enabling different telecommunication networks to communicate with each other. Designed…
Impersonating a mobile subscriber has become an increasingly discussed topic in telecommunications security, especially when techniques resemble SIM swap scenarios. At the heart of many of these threats lies the SS7 Server, a critical component in global mobile communications infrastructure. The notoriety of SS7-related attacks highlights the system’s vulnerabilities, with methods like subscriber impersonation drawing attention from both security professionals and malicious actors. Understanding how these techniques work is essential for anyone interested in how modern networks can be exploited. Understanding the Underlying Protocols The SS7 signaling protocol, known as Signaling System No. 7, is the backbone of most of the world’s public switched telephone networks. Designed decades ago, its…
In the digital era, Instagram has become a primary platform for sharing moments, conducting business, and connecting with communities. However, the popularity of Instagram brings increased risks, including sophisticated hacking techniques targeting user accounts. One particularly notable method that has emerged is Instagram hacking via SS7, which exploits weaknesses in telecommunications infrastructure to breach user security. Understanding how SS7 vulnerabilities can be used to intercept and compromise Instagram accounts is crucial for anyone with an online presence. This article explores what SS7 is, how hackers can leverage its flaws, and why it presents a significant concern for Instagram users. What Is SS7 and Why Does It Matter? SS7, or Signaling…
The topic of WhatsApp hacking via SS7 draws significant attention as messaging app security becomes increasingly crucial. SS7 Server vulnerabilities pose risks to users by potentially exposing private chats and important account details. WhatsApp, being one of the world’s most popular messaging platforms, is a prime target for various hacking strategies. One such method exploits the SS7 protocol, which is vital in the functioning of mobile networks. Understanding SS7 and Its Role in Telecommunication SS7, or Signaling System No. 7, is a collection of protocols essential for exchanging information between telecom networks. It allows mobile users to make calls, send texts, and move between networks without interruption. Designed decades ago,…
Instagram has become an integral part of daily life for millions around the globe, but as its popularity grows, so do the risks associated with its security. One advanced method gaining attention for its effectiveness in breaching Instagram accounts involves the SS7 Server. SS7, or Signaling System No. 7, is a set of protocols that’s fundamental to telecommunication networks, playing a crucial role in the way data and messages are transmitted. Understanding how SS7 is exploited is key to grasping the modern landscape of digital threats, especially on major platforms like Instagram. What is SS7 and Why Does it Matter? The SS7 protocol suite was first developed in the 1970s,…
In today’s interconnected world, communication networks operate on complex systems to deliver calls efficiently and securely. One of the most fundamental technologies at the core of these networks is the SS7 Server, which enables various types of call management and signaling. Understanding how SS7 Server functions in call monitoring is essential for grasping the inner workings of telecom infrastructure. Call monitoring via SS7 involves a blend of signaling and protocol analysis, ensuring seamless, fast, and intelligent routing of voice data. As telecom solutions continue to advance, the role of SS7 in monitoring calls becomes even more crucial for maintaining network quality and performance. The Basics of SS7 and Call Monitoring…
In recent years, the fascination with uncovering the inner workings of mobile communication networks has grown, particularly with the revelation that it is possible to eavesdrop on phone calls via SS7. The SS7 protocol plays a central role in how telecommunications networks communicate, but it has vulnerabilities that make such surveillance feasible. Understanding how this eavesdropping occurs is crucial for anyone concerned with their privacy. Exploring the mechanics behind these attacks offers insights into the world of telecom security and the significance of stronger protection measures. How SS7 Facilitates Phone Call Eavesdropping Signaling System 7, commonly referred to as SS7, is a protocol suite developed in the 1970s to facilitate…
The topic of Telegram hacking via SS7 is gaining attention among cybersecurity experts and privacy advocates. Telegram, renowned for its encryption and privacy standards, is not immune to sophisticated methods such as those involving a SS7 Server. While many users trust Telegram for secure messaging, the vulnerabilities in telecom infrastructure like SS7 can still place sensitive data at risk. Understanding how these attacks work is vital for anyone interested in digital privacy. What is SS7 and How Does it Work? The Signaling System 7, commonly referred to as SS7, is a set of protocols used by telecommunication networks worldwide. Its primary function is to manage how telephone calls and text…